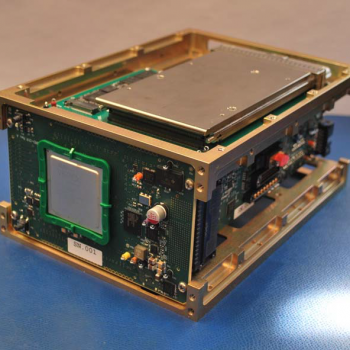
Lincoln Laboratory technologies named 2020 R&D 100 Award winners
Among the winners of the 2020 R&D 100 Awards were eight technologies developed by MIT Lincoln Laboratory researchers, either wholly or in collaboration with researchers from other organizations. Annually since 1963, these international R&D awards have recognized 100 technologies that a panel of expert judges selected as the most revolutionary of the past year.
Six of the Laboratory's winning technologies are software systems, a number of which take advantage of artificial intelligence techniques. The software technologies are solutions to difficulties inherent in analyzing large volumes of data and to problems in maintaining cybersecurity. Another technology is a process designed to assure secure fabrication of integrated circuits, and the eighth winner is an optical communications technology that may enable future space missions to transmit error-free data to Earth at significantly higher rates than currently possible.
- To enable timely, effective responses to post-disaster large-scale power outages, Lincoln Laboratory created a system that rapidly estimates and maps the extent and location of power outages across geographic boundaries. Cyber Sensing for Power Outage Detection, nicknamed CyberPow, uses pervasive, Internet-connected devices to produce near-real-time situational awareness to inform decisions about allocating personnel and resources. The system performs active scanning of the IP networks in a targeted region to identify changes in network device availability as an indicator of power loss. CyberPow is a low-cost, efficient alternative to current approaches that rely on piecing together outage data from disparate electric utilities with varying ability to assess their own outages.
- The Forensic Video Exploitation and Analysis (FOVEA) tool suite, developed by the Laboratory under the sponsorship of the Department of Homeland Security Science and Technology Directorate, enables users to efficiently analyze video captured by existing large-scale closed-circuit television systems. The FOVEA tools expedite daily tasks, such as searching through video, investigating abandoned objects, or piecing together activity from multiple cameras. A video summarization tool condenses all motion activity within a long timeframe into a very short visual summary, transforming, for example, one hour of raw video into a three-minute summary that also acts as a clickable index into the original video sequence. To allow analysts to track the onsite history of a suspicious object, a "jump back" feature automatically scans to the segment of video in which an idle or suspicious object first appeared. Because analysts can quickly navigate a camera network through the use of transition zones — clickable overlays that mark common entry/exit zones — FOVEA makes it easy to follow a person of interest through many camera views. Video data from each camera combined on the fly in chronological order can be exported easily. Highly efficient algorithms mean that no specialized hardware is required; thus, FOVEA software tools can add strong forensic capabilities to any video streaming system.

- Keylime is an open-source key bootstrapping and integrity management software architecture designed to increase the security and privacy of Edge, Cloud, and Internet of Things (IoT) devices. Keylime enables users to securely upload cryptographic keys, passwords, and certificates into their machines without unnecessarily divulging these secrets. In addition, Keylime enables users to continuously verify trust in their computing resources without relying on their service providers to guarantee security. Keylime leverages the Trusted Platform Module, an industry-standard hardware security chip, but eliminates the complexity, compatibility, and performance issues that the module introduces. Keylime has fostered a vibrant, growing open-source community with the help of Red Hat, a multinational software company, and has been accepted as a Sandbox technology in the Cloud Native Computing Foundation, a Linux Foundation project.
- A team from Lincoln Laboratory, New York University, and Northeastern University developed the Large-scale Vulnerability Addition (LAVA) technique that injects numerous bugs into a program to create ground truth for evaluating bug-finding systems. The technique inserts bugs at known locations in a program and constructs triggering inputs for each bug. A bug finder’s ability to discover LAVA bugs in a program can be used to estimate the finder's false negative and false positive rates. LAVA addresses the critical need for technology that can discover new approaches to finding bugs in software programs. Despite decades of research into building stable software, bugs still plague modern programs, and current approaches to bug discovery have relied on analyzing programs against programs that have either no known bugs or previously discovered bugs. Manually creating programs with known bugs is laborious and cannot be done at a large scale. LAVA is the only system capable of injecting essentially an unlimited number of bugs into real programs given the program's source code. It has been used to evaluate bug finders, both human and automated, since 2017.
- The Reconnaissance of Influence Operations (RIO) software system automates the detection of disinformation narratives, networks, and influential actors. The system is designed to address the growing threat posed by adversarial countries that exploit social media and digital communications to achieve political objectives. The unprecedented scales, speeds, and reach of disinformation campaigns present a rising threat to global stability, and especially to democratic societies. The RIO system integrates natural language processing, machine learning, graph analytics, and novel network causal inference to quantify the impact of individual actors in spreading the disinformation narrative. By providing situational awareness of influence campaigns and knowledge of the mechanisms behind social influence, RIO offers capabilities that can aid in crafting responses to dangerous influence operations.

- Many popular closed-source computer applications like browsers or productivity applications running on the Windows operating system are vulnerable to large-scale cyber attacks through which adversaries use previously discovered entry into the applications' data to take control of a computer. Enabling the severity of these attacks is the homogeneity of the targets: because all installations of an application look alike, it can be easy for attackers to simultaneously compromise millions of computers, remotely exfiltrating sensitive information or stealing user data. Lincoln Laboratory's Timely Randomization Applied to Commodity Executables at Runtime (TRACER) technique protects closed-source Windows applications against sophisticated attacks by automatically and transparently re-randomizing the applications’ sensitive internal data and layout every time any output is generated. TRACER therefore assures that leaked information quickly becomes stale and that attacks cannot bypass a one-time randomization as is the case in one-time randomization defenses.
- Lincoln Laboratory researchers developed the Defensive Wire Routing for Untrusted Integrated Circuit Fabrication techniques to deter an outsourced foundry from maliciously tampering with or modifying the security-critical components of a digital circuit design. For example, a trusted design could be changed by a fabricator who inserts a "hardware Trojan" or "backdoor" that can compromise the downstream system security. The Defensive Wire Routing technology augments standard wire routing processes to make complex integrated circuits (ICs) inspectable and/or tamper evident post fabrication. The need for such defensive techniques has arisen because of increasing commercial and government use of outsourced third-party IC foundries for advanced high-performance IC fabrication.

-
Sponsored by NASA, Lincoln Laboratory developed TeraByte InfraRed Delivery (TBIRD), a technology that enables error-free transmission of data from satellites in low Earth orbit (LEO) at a rate of 200 gigabits per second. The current approach to LEO data delivery, generally a combination of RF communication, networks of ground stations, and onboard data compression, will become less able to efficiently and accurately handle the volume of data sent from the increasing numbers of LEO satellites sharing a crowded RF spectrum. TBIRD is an optical communications alternative that leverages the high bandwidths and unregulated spectrum available in the optical frequencies. It combines a custom-designed, innovative transmit/receive system in conjunction with commercial transceivers to provide high-rate, error-free data links through the dynamic atmosphere. Because TBIRD enables extremely high data-volume transfers that can occur over different atmospheric conditions (horizontal-link or LEO-to-ground), it has the potential to transform satellite operations in all scientific, commercial, and defense applications.
Because of the COVID-19 pandemic, editors of R&D World, an online publication that promotes the award program, announced the winners at virtual ceremonies broadcast on September 29 and 30 and October 1. Since 2010, Lincoln Laboratory has had 66 technologies recognized with R&D 100 Awards.